ShadowMove: a Stealthy Lateral Movement Strategy
Advanced persistent threat (APT) attacks pose serious threats to the security of mission-critical enterprise systems. Such attacks often use spearphishing or watering hole attacks to find a foothold within target networks; then they use the compromised systems as stepping stones to reach other systems until they gain access to the critical assets (such as a file server containing confidential documents), buried deep inside the networks. This incremental movement toward the critical systems is called lateral movement. For example, during the Equifax breach, the attackers first compromised a consumer complaint web portal; from that computer they gleaned saved passwords for accounts on other internal systems of Equifax; then they used those passwords to log into other systems, from which they discovered and exfiltrated personal data of 143 million people.
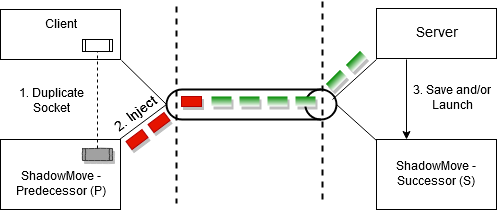
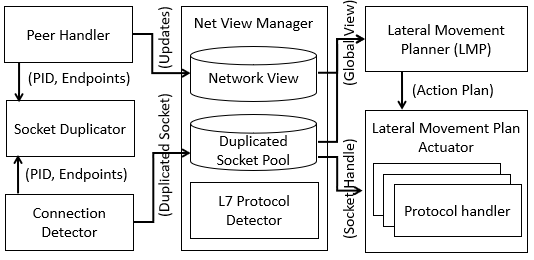
In this project, we carry out the first systematic study on a novel lateral movement strategy, called ShadowMove, which is easy to carry out but can cause serious damage. ShadowMove enables attackers to move stealthily among computers in enterprise networks without being detected by existing host-level and network-level defensive mechanisms. In this attack scenario, attackers passively observe communication dynamics of the compromised nodes to gradually construct their model of normal behaviors in the target network and utilize this model to choose the next victim node. Moreover, to make the attack stealthier, attackers restrict themselves to reuse only established connections. Many application protocols such as WinRM (Windows Remote Management) allow users to perform some operations on the remote server. Attackers inject their own commands in the command streams of such protocols to achieve their goals. For example, attackers can execute a program remotely by injecting commands in an established WinRM session.


ShadowMove makes APT attacks easier and thus more effective in a number of ways. Unlike hijacking attacks that inject code into legitimate client processes to reuse their connections, ShadowMove does not inject any code in benign clients. Instead, it employs a novel technique to secretly duplicate sockets owned by legitimate clients and injects commands through such duplicated sockets. By doing so, no new connection needs to be created; and for the same reason, no new authentication is necessary as the injected commands are interpreted in the context of already established sessions, which avoids the collection of user credentials, a typical APT attack step. ShadowMove takes advantage of two fundamental weaknesses in existing computing environments: the first one stems from the conflicting requirements between process isolation and resource sharing in commodity operating systems, which allows the attack process to duplicate (share) sockets belonging to legitimate client processes; and the second one arises from a lack of built-in message origin integrity validation mechanisms in many networking protocols, which enables the attack process to inject malicious packets (in existing connections) that cannot be differentiated from legitimate request packets.
Publication and Presentation: